
Quantum Key Distribution
Information-theoretically secure key exchange guaranteed by the laws of quantum physics

Information-theoretically secure key exchange guaranteed by the laws of quantum physics
Taqbit offers two complementary QKD protocols optimized for different deployment scenarios, both providing mathematically proven security against all computational attacks.
Coherent-One-Way QKD uses weak coherent pulses with time-bin encoding and a dedicated monitoring line to detect eavesdropping. The protocol offers an optimal balance between implementation simplicity and high performance.
Differential-Phase-Shift QKD encodes information in the relative phase between consecutive photon pulses, offering higher key-generation rates and stable operation over long distances.
| Feature | COW QKD | DPS QKD |
|---|---|---|
| Protocol | Coherent-One-Way | Differential-Phase-Shift |
| Encoding Method | Time-bin encoding | Phase difference encoding |
| Key Rate (at 22dB loss) | ~1 kbps | ~2 kbps |
| Max Distance | >100 km | >100 km |
| Eavesdrop Detection | Monitoring line statistics | Phase correlation analysis |
| Best For | Metro networks, moderate distances | Long-haul, high-throughput links |
The science behind our unbreakable quantum encryption
Unlike classical encryption that relies on computational complexity, QKD's security is guaranteed by the fundamental laws of quantum physics. Any attempt to measure quantum states disturbs them (Heisenberg Uncertainty Principle), making eavesdropping detectable.
Quantum Uncertainty
Measuring quantum states inevitably alters them, revealing eavesdroppers
No-Cloning Theorem
Quantum states cannot be perfectly copied, preventing undetected interception

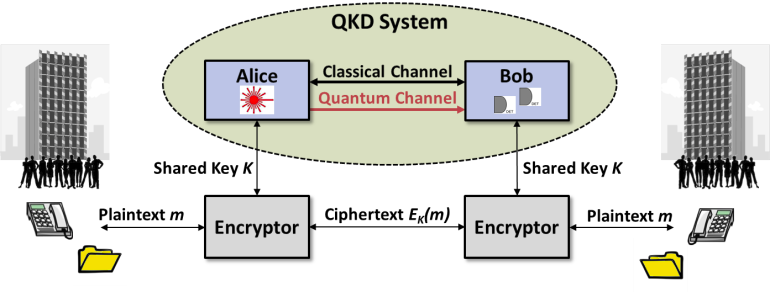
Alice encodes random bits in quantum states (photons) and sends them to Bob through a quantum channel (optical fiber)
Bob measures the incoming quantum states, then both parties reconcile detected measurements
Parties compare a subset of bits to estimate quantum bit error rate (QBER) and detect potential eavesdropping
Error correction and privacy amplification algorithms produce a final secure key with proven secrecy
Flexible integration options for your security infrastructure
Secure links between data centers with rack-mounted QKD terminals and key management systems
Point-to-point quantum-secured links for metropolitan area networks and financial exchanges
Trusted node networks for national-scale quantum-secured communication infrastructure